1. CentOS7
[ Apache Server ]
yum -y install mod_ssl
yum -y install openssl
mkdir -p /app/ssl
# ROOT CA 개인키 생성
openssl genrsa -aes256 -passout pass:P@ssw0rd! -out /app/ssl/rootca.key 2048
chmod 600 /app/ssl/rootca.key
# ROOT CA 인증요청서 생성
cat <<APACHE_SSL_SETTING > /app/ssl/rootca.conf
[ req ]
default_bits = 2048
default_md = sha1
default_keyfile = rootca.key
distinguished_name = req_distinguished_name
extensions = v3_ca
req_extensions = v3_ca
[ v3_ca ]
basicConstraints = critical, CA:TRUE, pathlen:0
subjectKeyIdentifier = hash
##authorityKeyIdentifier = keyid:always, issuer:always
keyUsage = keyCertSign, cRLSign
nsCertType = sslCA, emailCA, objCA
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = KR
countryName_min = 2
countryName_max = 2
# 회사명 입력
organizationName = Organization Name (eg, company)
organizationName_default = HMWOO Inc.
# 부서 입력
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = HMWOO Developer Team
# SSL 인증서 발급자 명 입력
commonName = Common Name (eg, your name or your server's hostname)
commonName_default = HMWOO Self Signed CA
commonName_max = 64
APACHE_SSL_SETTING
echo -e "\n\n\n\n" | openssl req -new -key /app/ssl/rootca.key -passin pass:P@ssw0rd! -out /app/ssl/rootca.csr -config /app/ssl/rootca.conf
# ROOT CA 인증서 생성
openssl x509 -req -days 3650 -extensions v3_ca -set_serial 1 -in /app/ssl/rootca.csr -signkey /app/ssl/rootca.key -passin pass:P@ssw0rd! -out /app/ssl/rootca.crt -extfile /app/ssl/rootca.conf
# ROOT CA 정보 확인
openssl x509 -text -in /app/ssl/rootca.crt
# 서버 개인키 생성
openssl genrsa -aes256 -passout pass:P@ssw0rd! -out /app/ssl/server.key 2048
# 서버 개인키 패스워드 제거
cp /app/ssl/server.key /app/ssl/server.key.origin
openssl rsa -in /app/ssl/server.key.origin -passin pass:P@ssw0rd! -out /app/ssl/server.key
chmod 600 /app/ssl/server.*
# 서버 인증요청서 생성
cat <<APACHE_SSL_SETTING > /app/ssl/server.conf
[ req ]
default_bits = 2048
default_md = sha1
default_keyfile = server.key
distinguished_name = req_distinguished_name
extensions = v3_user
[ v3_user ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
authorityKeyIdentifier = keyid,issuer
subjectKeyIdentifier = hash
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
## SSL 용 확장키 필드
extendedKeyUsage = serverAuth,clientAuth
subjectAltName = @alt_names
[ alt_names ]
## Subject AltName의 DNSName field에 SSL Host 의 도메인 이름을 적어준다.
DNS.1 = www.hmwoo.com
DNS.2 = hmwoo.com
DNS.3 = *.hmwoo.com
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = KR
countryName_min = 2
countryName_max = 2
# 회사명 입력
organizationName = Organization Name (eg, company)
organizationName_default = HM Inc.
# 부서 입력
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = HM SSL Project
# SSL 서비스할 domain 명 입력
commonName = Common Name (eg, your name or your server's hostname)
commonName_default = hmwoo.com
commonName_max = 64
APACHE_SSL_SETTING
echo -e "\n\n\n\n" | openssl req -new -key /app/ssl/server.key -out /app/ssl/server.csr -config /app/ssl/server.conf
# 서버 인증서 생성( 365 * 5 = 1825 )
openssl x509 -req -days 1825 -extensions v3_user -in /app/ssl/server.csr -CA /app/ssl/rootca.crt -CAcreateserial -CAkey /app/ssl/rootca.key -passin pass:P@ssw0rd! -out /app/ssl/server.crt -extfile /app/ssl/server.conf
# 인증서 정보 확인
openssl x509 -text -in /app/ssl/server.crt
cat <<APACHE_SSL_SETTING > /etc/httpd/conf.d/ssl.conf
Listen 443 https
SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog
SSLSessionCache shmcb:/run/httpd/sslcache(512000)
SSLSessionCacheTimeout 300
SSLCryptoDevice builtin
<VirtualHost *:443>
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW
SSLCertificateFile /app/ssl/server.crt
SSLCertificateKeyFile /app/ssl/server.key
SSLCACertificateFile /app/ssl/rootca.crt
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
CustomLog logs/ssl_request_log \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
APACHE_SSL_SETTING
sed -i '/^<IfModule\s*mod_rewrite.c>/,/<\/IfModule>/d' /etc/httpd/conf/httpd.conf
cat <<APACHE_SSL_SETTING >> /etc/httpd/conf/httpd.conf
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTPS} !on
RewriteRule ^(.*)$ https://%{HTTP_HOST}$1 [R,L]
</IfModule>
APACHE_SSL_SETTING
systemctl restart httpd
firewall-cmd --permanent --add-port=443/tcp
firewall-cmd --permanent --add-port=80/tcp
firewall-cmd --reload
firewall-cmd --list-ports
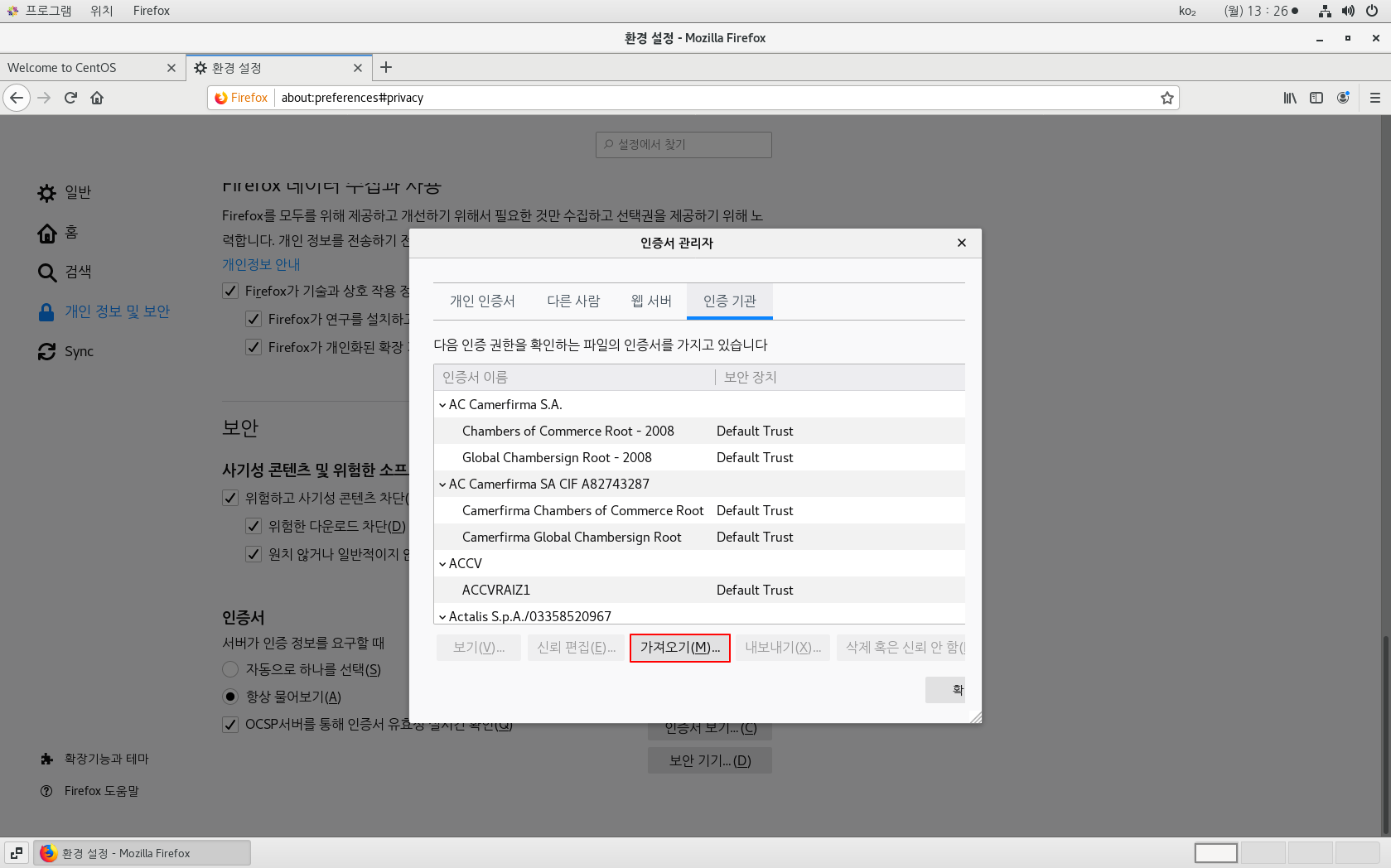
[ Linux Client ]






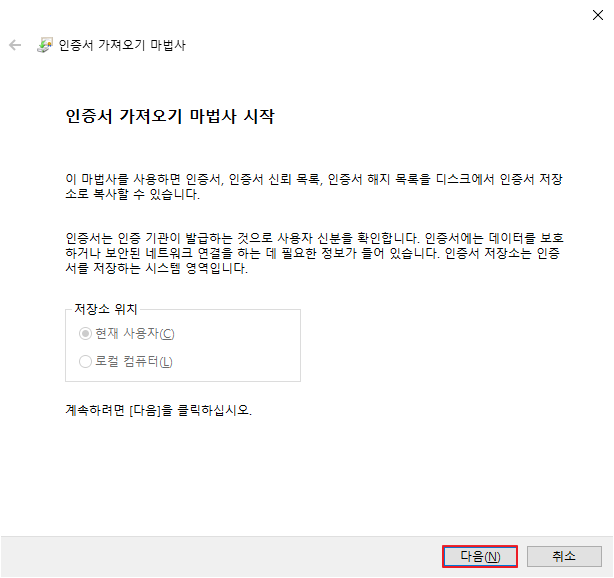
[ Window Client ]









'Operating Systems > Linux' 카테고리의 다른 글
| [ Linux ] Tomcat 컨테이너 추가 (0) | 2023.01.22 |
|---|---|
| [ Linux ] APACHE 서버 설치 (0) | 2023.01.18 |
| [ Linux ] KALI 리눅스 설치 (0) | 2021.11.27 |
| [ Linux ] SNORT 서버 설치 (0) | 2021.11.25 |
| [ Linux ] 방화벽 서버 설치 (0) | 2021.11.20 |
